在采集程序中增加定时发送邮件以及关机处理的实现
我们在采集特定数据的时候,往往需要耗费较长的时间,有时候因为一些事情,不可能长久的在电脑前等待结果,那么需要程序在一段时间后自动给我们发送邮件等通知,以及执行退出程序或者关机等处理善后工作,以节省资源或者电源,那么需要实现这个过程是如何的呢。本篇随笔基于这个采集程序的基础上增加这些功能的实现,介绍其中的一些处理技巧。
1、邮件配置
如果我们需要实现发送邮件、或者发送短信等通知途径,那么我们就需要把这些处理过程涉及到的参数提前录入到系统里面,是在不行硬编码也行,不过为了可扩展性,我倾向于使用配置界面进行参数的配置。
在关于参数配置的处理,我在博客《
Winform开发框架之参数配置管理功能实现-基于SettingsProvider.net的构建
》以及《
Winform界面中实现菜单列表的动态个性化配置管理
》都做了比较详细的介绍,基于SettingsProvider.net的封装处理,能够实现我们很方便的配置功能,可以配置在XML文件中,也可以保存在数据库中,根据需要处理。
那么我这里为了采集发送数据的需要,也需要配置一个邮件的信息,如下界面所示。
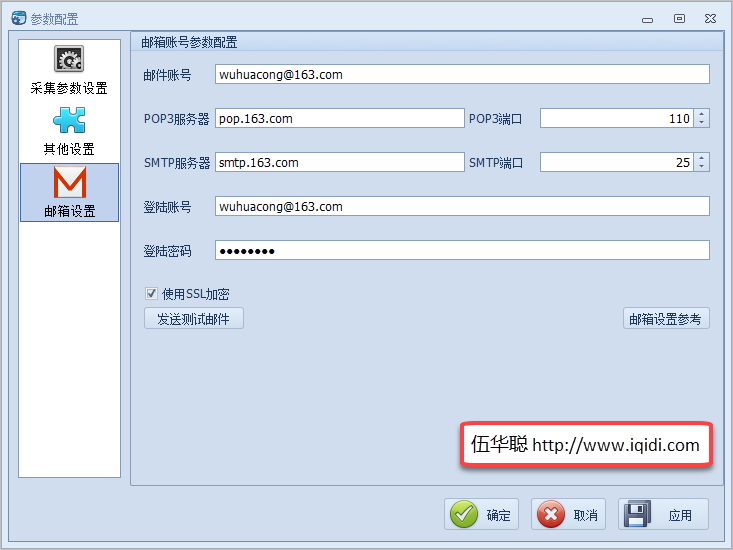
这个里面放置额外的两个功能按钮,一个是邮箱设置参考,一个是发送测试邮件,前者用来辅助填入一些参数,后者是验证用户账号是否收到测试邮件。

发送测试邮件成功后,我们验证下是否收到,以便核对下提供的参数是否正确。

2、设置定时处理
完成上面的步骤后,我们基本上完成了一半的工作量了,剩下的就是在合适的时间,让系统发送通知给我们以及善后处理即可。
那么我们如果定时的话,需要指定一个时间范围,使用DevExpress的TimeSpanEdit控件就合适不过了,我们只需要确定小时:分钟:秒的数据后,就可以根据这个时间范围确定我们执行任务的最终时间了。

这个弹出的小窗体,我们只用来获取用户输入的时间范围即可,没有什么具体的逻辑。
输入关机时间后,那么我们就可以根据关机时间,弹出一个倒计时的窗体,覆盖在主程序的界面上。
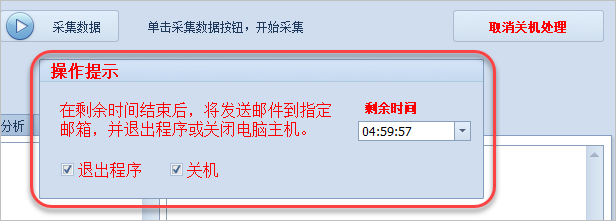
最终我们到达时间的触发点后,实现发送邮件通知以及退出程序或者关机的处理。
以上是整个处理的过程,那么实现的处理代码是如何的呢,我们来分析下具体的代码过程。
private bool isShutdown = false;privateTimerHelper timerHelper;private void btnSendAndShutdown_Click(objectsender, EventArgs e)
{
btnSendAndShutdown.Enabled= false;try{if (!isShutdown)
{//获取关机的时间 FrmShutdownTime frmTime = newFrmShutdownTime();if (frmTime.ShowDialog() !=System.Windows.Forms.DialogResult.OK)return;//转换为最终的时间 TimeSpan timeSpan =frmTime.timeShutdown.TimeSpan;this.endTime =DateTime.Now.Add(timeSpan);//定时器辅助类处理定时工作 timerHelper = new TimerHelper(1000, true);
timerHelper.Execute+= () =>{//每隔一秒对事件进行处理判断 if (ShutdownEvent != null)
{
ShutdownEvent(sender, e);
}
};//显示关机面板 groupShutdown.BringToFront();
groupShutdown.Visible= true;
}else{//关闭面板 CloseShutDownGroup();
}
isShutdown= !isShutdown;this.btnSendAndShutdown.Text = isShutdown ? "取消关机处理" : "定时发送邮件后关机";
}finally{
btnSendAndShutdown.Enabled= true;
}
}
上面主要的处理逻辑,放在了定时器的处理事件上
ShutdownEvent(sender, e);
这个触发的事件,是我们在主窗体定义的一个事件,目的就是用来实现倒计时及发送通知用的。
private event EventHandler ShutdownEvent;
然后我们在窗体里面初始化这个事件处理即可,初始化代码如下所示。
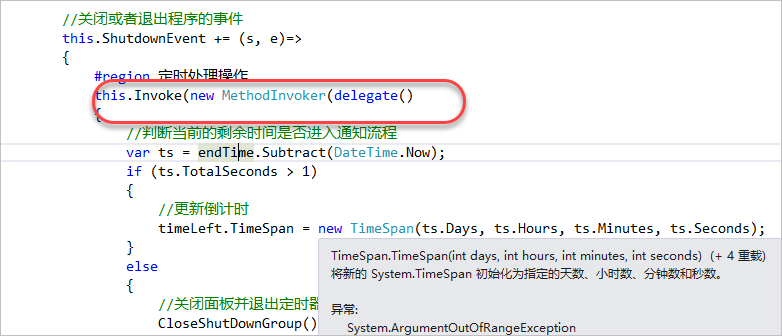
//关闭或者退出程序的事件 this.ShutdownEvent += (s, e)=>{#region 定时处理操作 this.Invoke(new MethodInvoker(delegate()
{//判断当前的剩余时间是否进入通知流程 var ts =endTime.Subtract(DateTime.Now);if (ts.TotalSeconds > 1)
{//更新倒计时 timeLeft.TimeSpan = newTimeSpan(ts.Days, ts.Hours, ts.Minutes, ts.Seconds);
}else{//关闭面板并退出定时器 CloseShutDownGroup();//执行发送邮件操作 SendMail();//关闭主机或者退出程序 if(chkShutdown.Checked)
{
Process.Start("shutdown.exe", "-s");//关机 }else if(chkExitApp.Checked)
{
Application.ExitThread();
}
}
}));#endregion
最终的逻辑就是发送邮件和退出程序或者关机的处理
//执行发送邮件操作 SendMail();//关闭主机或者退出程序 if(chkShutdown.Checked)
{
Process.Start("shutdown.exe", "-s");//关机 }else if(chkExitApp.Checked)
{
Application.ExitThread();
}
关机的操作,我们用来执行命令行的方式实现关机的处理,非常方便。
关于这个Shutdown命令的处理,我下面列出它的一些功能说明。
shutdown命令的参数:
shutdown.exe-s:关机
shutdown.exe-r:关机并重启
shutdown.exe-l:注销当前用户
shutdown.exe-s -t 时间:设置关机倒计时
shutdown.exe-h:休眠
shutdown.exe-t 时间:设置关机倒计时。默认值是 30秒。
shutdown.exe-a:取消关机
shutdown.exe-f:强行关闭应用程序而没有警告
shutdown.exe-m \计算机名:控制远程计算机
shutdown.exe-i:显示“远程关机”图形用户界面,但必须是Shutdown的第一个参数
shutdown.exe-c "消息内容":输入关机对话框中的消息内容
shutdown.exe-d [u][p]:xx:yy :列出系统关闭的原因代码:u 是用户代码 ,p 是一个计划的关闭代码 ,xx 是一个主要原因代码(小于 256 的正整数) ,yy 是一个次要原因代码(小于 65536的正整数)
比如你的电脑要在12:00关机,可以选择“开始→运行”,输入“at12:00 Shutdown -s",这样,到了12点电脑就会出现“系统关机”对话框,默认有30秒钟的倒计时并提示你保存工作。 如果你想以倒计时的方式关机,可以输入 “Shutdown.exe -s -t 3600",这里表示60分钟后自动关机,“3600"代表60分钟。
而发送邮件,我们一般利用一个邮件发送的封装类处理下即可。
/// <summary> ///发送邮件/// </summary> private boolSendMail()
{//统计数据 btnSumaryData_Click(null, null);string title = string.Format("{0}期统计结果-{1}", Portal.gc.CurrentQSNumber, DateTime.Now);//获取控件展示的内容,并把它的换行转换下 List<string> list = new List<string>();
list.AddRange(txtShenxiao.Lines);
list.AddRange(this.txtShenxiao2.Lines);string content = string.Join("<br>", list);//发送邮件 var success =SendMailHelper.SendMail(title, content);returnsuccess;
}
发送邮件的时候,我们先获取用户的邮件配置信息,然后调用邮件发送辅助类实现内容的发送处理,具体代码如下所示。
public classSendMailHelper
{/// <summary> ///发送邮件结果/// </summary> public static bool SendMail(string title, stringcontent)
{//获取配置的邮件信息 string creator = "";//LoginUserInfo.Name; ISettingsStorage store = newDatabaseStorage(creator);
SettingsProvider settings= newSettingsProvider(store);bool result = false;
EmailParameter parameter= settings.GetSettings<EmailParameter>();if (parameter != null)
{//使用邮件辅助类,实现邮件内容的发送 EmailHelper email = newEmailHelper(parameter.SmtpServer, parameter.LoginId, parameter.Password);
email.Subject=title;
email.Body=content;
email.IsHtml= true;
email.Charset= "gb2312";
email.From=parameter.Email;
email.FromName=parameter.Email;
email.AddRecipient(parameter.Email);
result=email.SendEmail();
}returnresult;
}
以上就是整个处理的过程,其中还涉及到了在线程间访问控件的方式,如下代码所示。
这个详细的介绍可以参考我较早期的随笔《
浅谈多线程中数据的绑定和赋值
》,这些细节都需要我们一步步测试并寻找最佳的方案实现,希望这个随笔的思路给你有一定的启发。
当然,如果系统做的比较大一些,系统化一些的话,还可以考虑利用EasyNetQ的这种方式实现信息的通知。
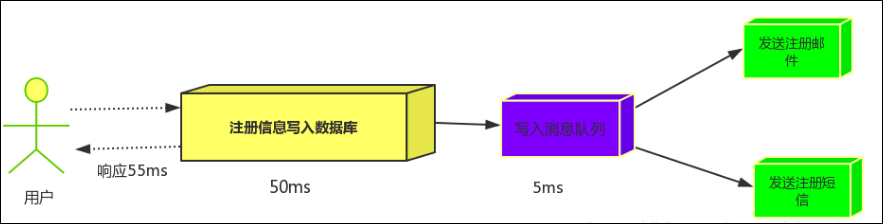
这种通知可以更好的扩展,详细介绍可以参考下随笔《
使用EasyNetQ组件操作RabbitMQ消息队列服务
》,不过一般小程序的就不用那么麻烦了,用一个定时器来处理下就可以了。