调试器工作流程
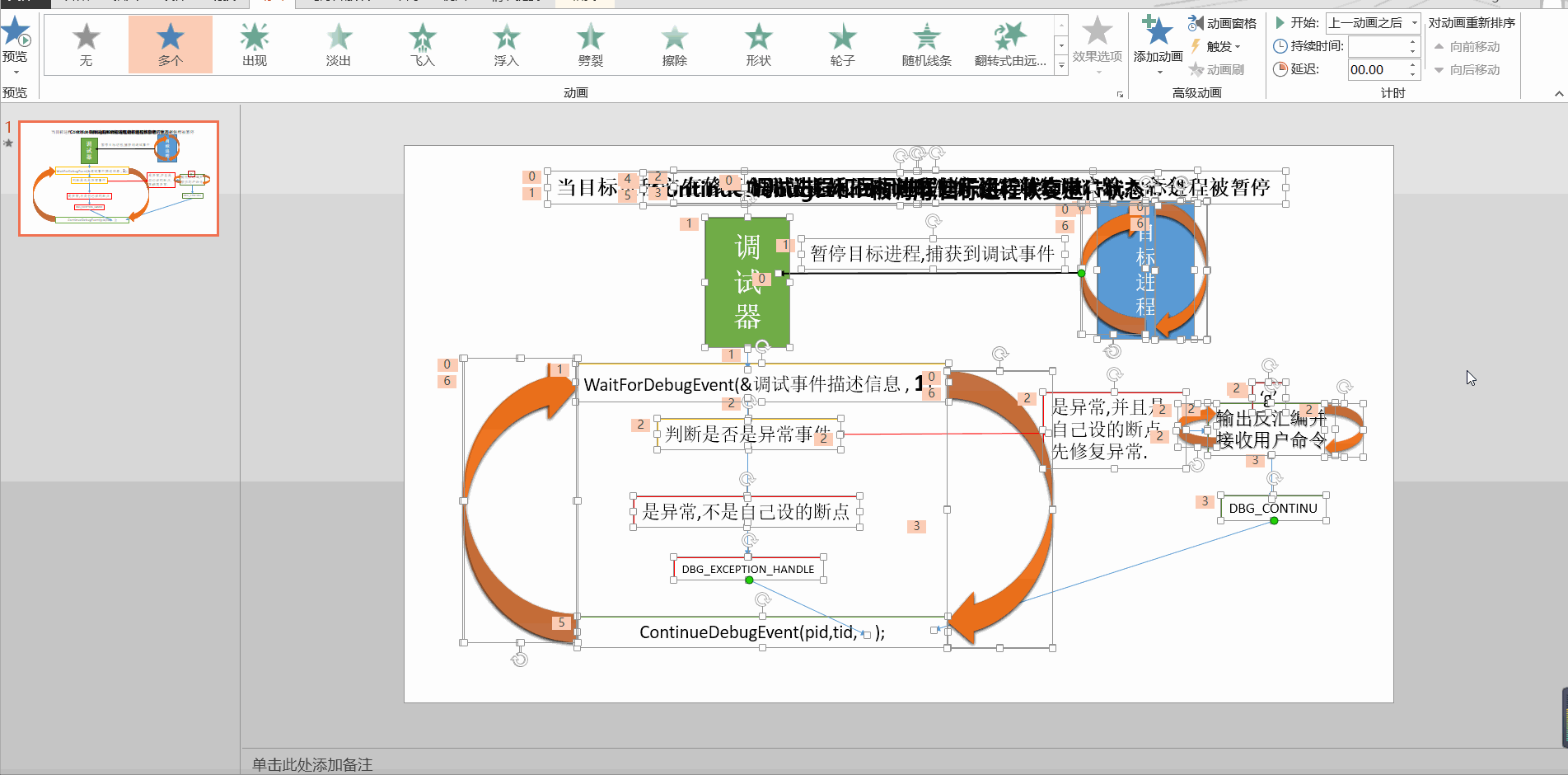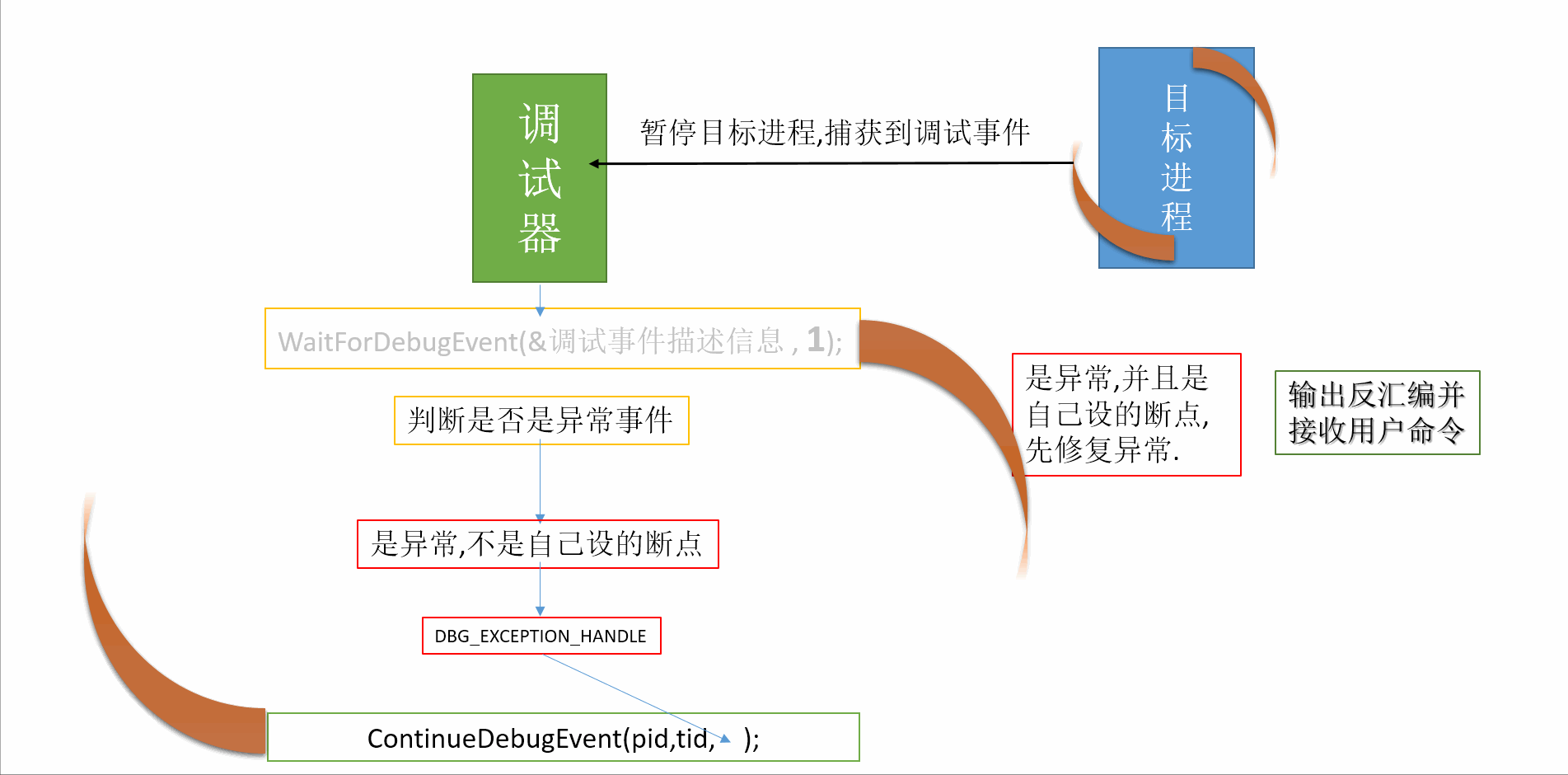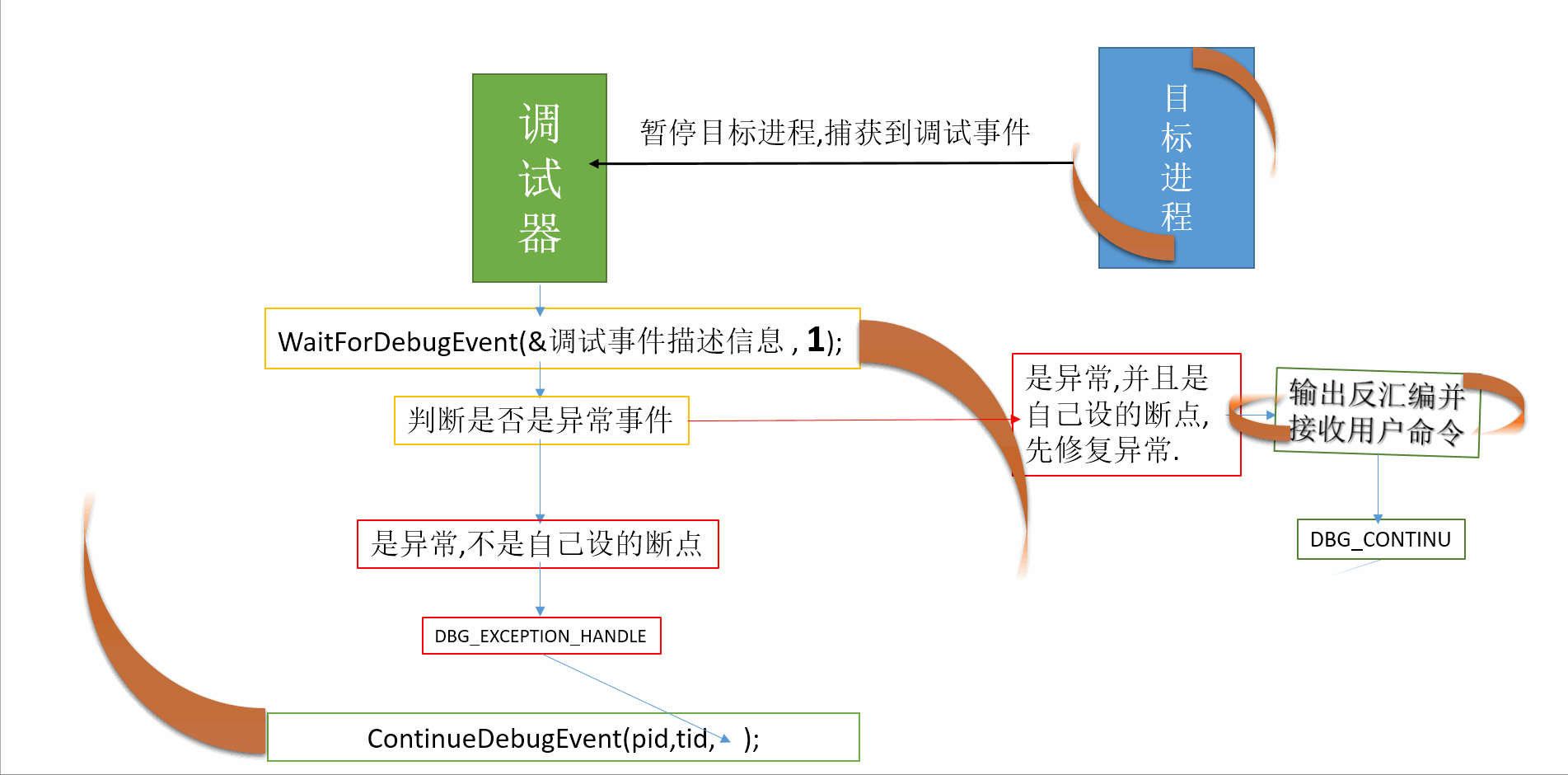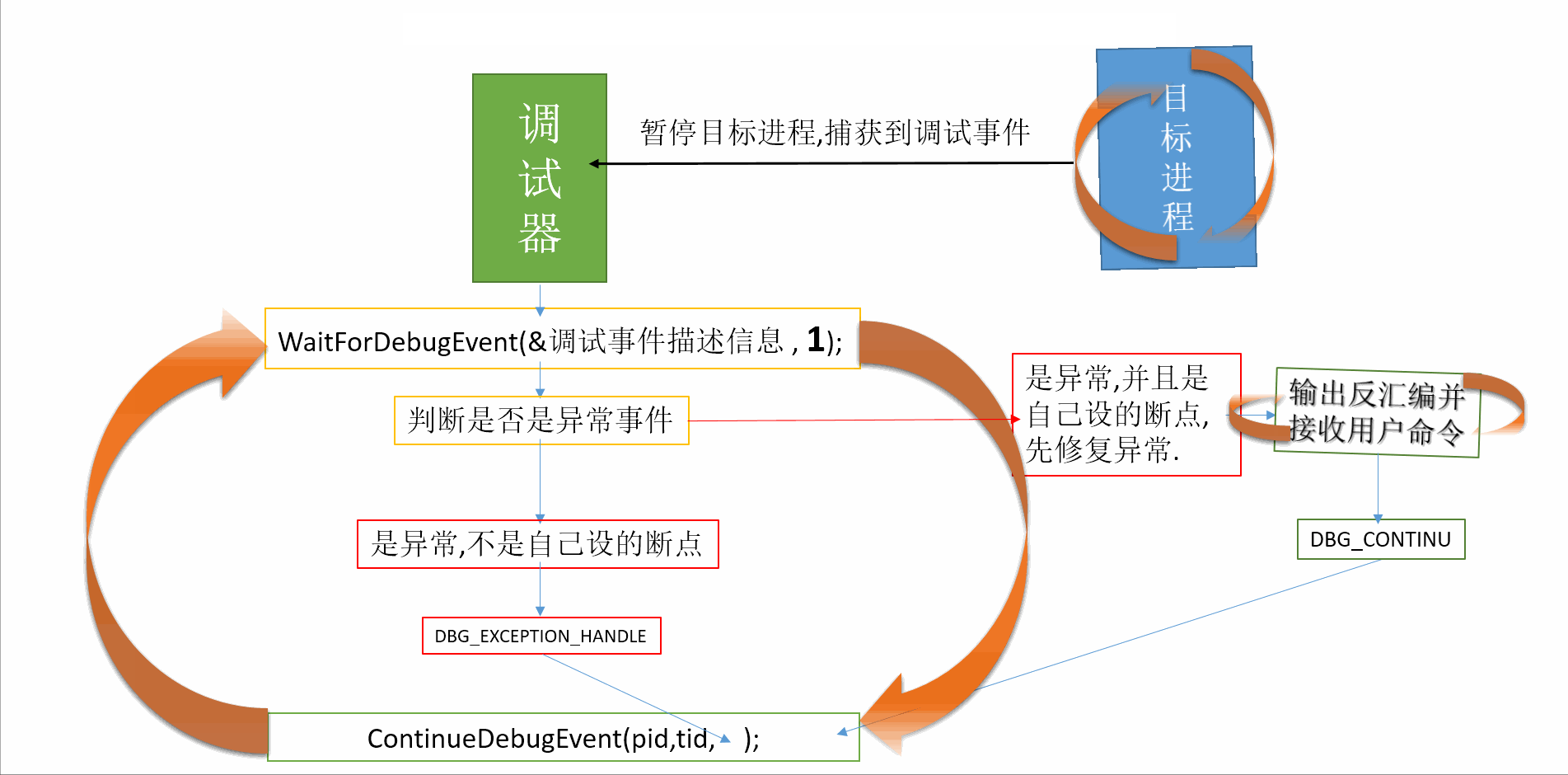
转自:https://blog.csdn.net/sinat_35360663/article/details/80176269

转自:https://blog.csdn.net/sinat_35360663/article/details/80176269
!dh扩展指令显示指定模块Image的头信息。相当于一个弱化的dumpbin工具。
!dh[Options]Address
!dh -h
以下任一选项:
显示文件头。
显示节头。
显示所有头信息.
指定Image的十六进制地址。
在调试器命令窗口中显示此扩展的一些帮助文本。
Windows 2000 |
|
Windows XP and later |
Dbghelp.dll |
!lmi扩展命令从Image头中提取最重要的信息,并以简明的摘要格式显示。而!dh更详细。
lmvm clr
Browse full module list
start end module name
153a0000 15a3d000 clr (deferred)
Image path: C:\Windows\Microsoft.NET\Framework\v4.0.30319\clr.dll
Image name: clr.dll
Browse all global symbols functions data
Timestamp: Sat Apr 12 09:25:50 2014 (5348961E)
CheckSum: 0069CE03
ImageSize: 0069D000
File version: 4.0.30319.34209
Product version: 4.0.30319.34209
File flags: 8 (Mask 3F) Private
File OS: 4 Unknown Win32
File type: 2.0 Dll
File date: 00000000.00000000
Translations: 0409.04b0
Information from resource tables:
CompanyName: Microsoft Corporation
ProductName: Microsoft® .NET Framework
InternalName: clr.dll
OriginalFilename: clr.dll
ProductVersion: 4.0.30319.34209
FileVersion: 4.0.30319.34209 built by: FX452RTMGDR
PrivateBuild: DDBLD354
FileDescription: Microsoft .NET Runtime Common Language Runtime - WorkStation
LegalCopyright: © Microsoft Corporation. All rights reserved.
Comments: Flavor=Retail
0:031>!dh -f 153a0000
File Type: DLL
FILE HEADER VALUES
14C machine (i386)
5 number of sections
5348961E time date stamp Sat Apr 12 09:25:50 2014
0 file pointer to symbol table
0 number of symbols
E0 size of optional header
2122 characteristics
Executable
App can handle >2gb addresses
32 bit word machine
DLL
OPTIONAL HEADER VALUES
10B magic #
11.00 linker version
639000 size of code
5DE00 size of initialized data
0 size of uninitialized data
CD8F8 address of entry point
1000 base of code
----- new -----
0f2b0000 image base
1000 section alignment
200 file alignment
2 subsystem (Windows GUI)
6.00 operating system version
10.00 image version
6.00 subsystem version
69D000 size of image
400 size of headers
69CE03 checksum
00100000 size of stack reserve
00001000 size of stack commit
00100000 size of heap reserve
00001000 size of heap commit
140 DLL characteristics
Dynamic base
NX compatible
9408 [ EDF] address [size] of Export Directory
64C7BC [ 8C] address [size] of Import Directory
650000 [ 504] address [size] of Resource Directory
0 [ 0] address [size] of Exception Directory
697200 [ 3E90] address [size] of Security Directory
651000 [ 4B4E8] address [size] of Base Relocation Directory
639F44 [ 54] address [size] of Debug Directory
0 [ 0] address [size] of Description Directory
0 [ 0] address [size] of Special Directory
0 [ 0] address [size] of Thread Storage Directory
18A960 [ 40] address [size] of Load Configuration Directory
0 [ 0] address [size] of Bound Import Directory
64C000 [ 7BC] address [size] of Import Address Table Directory
638E18 [ 260] address [size] of Delay Import Directory
0 [ 0] address [size] of COR20 Header Directory
0 [ 0] address [size] of Reserved Directory
0:031> !dh -s 153a0000
SECTION HEADER #1
.text name
638FFB virtual size
1000 virtual address
639000 size of raw data
400 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
60000020 flags
Code
(no align specified)
Execute Read
Debug Directories(3)
Type Size Address Pointer
cv 20 639f9c 63939c Format: RSDS, guid, 2, clr.pdb
( 12) 14 1e4390 1e3790
( 10) 4 639f98 639398
SECTION HEADER #2
.data name
11E9E virtual size
63A000 virtual address
EE00 size of raw data
639400 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
C0000040 flags
Initialized Data
(no align specified)
Read Write
SECTION HEADER #3
.idata name
3224 virtual size
64C000 virtual address
3400 size of raw data
648200 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
C0000040 flags
Initialized Data
(no align specified)
Read Write
SECTION HEADER #4
.rsrc name
504 virtual size
650000 virtual address
600 size of raw data
64B600 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
40000040 flags
Initialized Data
(no align specified)
Read Only
SECTION HEADER #5
.reloc name
4B4E8 virtual size
651000 virtual address
4B600 size of raw data
64BC00 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
42000040 flags
Initialized Data
Discardable
(no align specified)
Read Only
0:031> !dh -a 153a0000
File Type: DLL
FILE HEADER VALUES
14C machine (i386)
5 number of sections
5348961E time date stamp Sat Apr 12 09:25:50 2014
0 file pointer to symbol table
0 number of symbols
E0 size of optional header
2122 characteristics
Executable
App can handle >2gb addresses
32 bit word machine
DLL
OPTIONAL HEADER VALUES
10B magic #
11.00 linker version
639000 size of code
5DE00 size of initialized data
0 size of uninitialized data
CD8F8 address of entry point
1000 base of code
----- new -----
0f2b0000 image base
1000 section alignment
200 file alignment
2 subsystem (Windows GUI)
6.00 operating system version
10.00 image version
6.00 subsystem version
69D000 size of image
400 size of headers
69CE03 checksum
00100000 size of stack reserve
00001000 size of stack commit
00100000 size of heap reserve
00001000 size of heap commit
140 DLL characteristics
Dynamic base
NX compatible
9408 [ EDF] address [size] of Export Directory
64C7BC [ 8C] address [size] of Import Directory
650000 [ 504] address [size] of Resource Directory
0 [ 0] address [size] of Exception Directory
697200 [ 3E90] address [size] of Security Directory
651000 [ 4B4E8] address [size] of Base Relocation Directory
639F44 [ 54] address [size] of Debug Directory
0 [ 0] address [size] of Description Directory
0 [ 0] address [size] of Special Directory
0 [ 0] address [size] of Thread Storage Directory
18A960 [ 40] address [size] of Load Configuration Directory
0 [ 0] address [size] of Bound Import Directory
64C000 [ 7BC] address [size] of Import Address Table Directory
638E18 [ 260] address [size] of Delay Import Directory
0 [ 0] address [size] of COR20 Header Directory
0 [ 0] address [size] of Reserved Directory
SECTION HEADER #1
.text name
638FFB virtual size
1000 virtual address
639000 size of raw data
400 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
60000020 flags
Code
(no align specified)
Execute Read
Debug Directories(3)
Type Size Address Pointer
cv 20 639f9c 63939c Format: RSDS, guid, 2, clr.pdb
( 12) 14 1e4390 1e3790
( 10) 4 639f98 639398
SECTION HEADER #2
.data name
11E9E virtual size
63A000 virtual address
EE00 size of raw data
639400 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
C0000040 flags
Initialized Data
(no align specified)
Read Write
SECTION HEADER #3
.idata name
3224 virtual size
64C000 virtual address
3400 size of raw data
648200 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
C0000040 flags
Initialized Data
(no align specified)
Read Write
SECTION HEADER #4
.rsrc name
504 virtual size
650000 virtual address
600 size of raw data
64B600 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
40000040 flags
Initialized Data
(no align specified)
Read Only
SECTION HEADER #5
.reloc name
4B4E8 virtual size
651000 virtual address
4B600 size of raw data
64BC00 file pointer to raw data
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
42000040 flags
Initialized Data
Discardable
(no align specified)
Read Only
_IMAGE_EXPORT_DIRECTORY 153a9408 (size: 00000edf)
Name: clr.dll
Characteristics: 00000000 Ordinal base: 22.
Number of Functions: 116. Number of names: 115. EAT: 153a9430.
ordinal hint target name
33 0 15645AB2 AttachProfiler
34 1 15585AC2 CertCreateAuthenticodeLicense
35 2 1558591F CertFreeAuthenticodeSignerInfo
36 3 155858EC CertFreeAuthenticodeTimestamperInfo
37 4 1558597F CertTimestampAuthenticodeLicense
38 5 15585A11 CertVerifyAuthenticodeLicense
39 6 157DCC8A ClearDownloadCache
40 7 15507931 ClrCreateManagedInstance
41 8 1562CB25 CoEEShutDownCOM
42 9 1562862F CoInitializeCor
43 10 1562D1B6 CoInitializeEE
44 11 1562868F CoUninitializeCor
45 12 153B9C20 CoUninitializeEE
46 13 157EF53E CompareAssemblyIdentity
47 14 157EEBAA CompareAssemblyIdentityWithConfig
48 15 154E3B63 CopyPDBs
25 16 16666660E29 CorDllMainForThunk
49 17 1562CCE4 CorExitProcess
50 18 1564772A CorLaunchApplication
51 19 1562868F CorMarkThreadInThreadPool
52 20 15585E81 CreateActContext
53 21 154A1369 CreateApplicationContext
54 22 157DDCC6 CreateAssemblyCache
55 23 157EE6A1 CreateAssemblyConfigCookie
56 24 157DFDDD CreateAssemblyEnum
57 25 153CFBED CreateAssemblyNameObject
58 26 15585E4E CreateCMSFromXml
59 27 156591AA CreateHistoryReader
60 28 157E0AB5 CreateInstallReferenceEnum
61 29 157DD635 DeleteShadowCache
62 30 157EE83E DestroyAssemblyConfigCookie
63 31 153BAEB8 DllCanUnloadNowInternal
64 32 15469450 DllGetActivationFactoryImpl
65 33 154C3F53 DllGetClassObjectInternal
66 34 153B94C8 DllRegisterServerInternal
67 35 153AB7B4 DllUnregisterServerInternal
68 36 1562E3B8 EEDllRegisterServer
69 37 1562E55B EEDllUnregisterServer
26 38 15638ACB GetAddrOfContractShutoffFlag
70 39 15585EAD GetAppIdAuthority
71 40 157F2840 GetAssemblyIdentityFromFile
72 41 1562858D GetAssemblyMDImport
27 42 154ABE09 GetCLRFunction
73 43 157F4F59 GetCLRIdentityManager
74 44 157E16F4 GetCachePath
28 45 15642F7D GetClassActivatorForApplicationImpl
75 46 158151C9 GetHashFromAssemblyFile
76 47 1581533A GetHashFromAssemblyFileW
77 48 1581571D GetHashFromBlob
78 49 1581544F GetHashFromFile
79 50 15815524 GetHashFromFileW
80 51 158155FE GetHashFromHandle
81 52 156591AA GetHistoryFileDirectory
82 53 154BBC81 GetIdentityAuthority
83 54 1540E2E4 GetMetaDataInternalInterface
84 55 1551F885 GetMetaDataInternalInterfaceFromPublic
85 56 154E325C GetMetaDataPublicInterfaceFromInternal
86 57 1565563B GetPermissionRequests
87 58 15452955 GetPrivateContextsPerfCounters
88 59 15585DE9 GetUserStateManager
89 60 15585DBB GetUserStore
90 61 154C02CF IEE
91 62 154BB26C InitializeFusion
92 63 153B94C8 InstallCustomModule
94 64 1581ACEA LegacyNGenCompile
95 65 1581AA2E LegacyNGenCreateZapper
96 66 1581ABB6 LegacyNGenFreeZapper
97 67 1581AC37 LegacyNGenTryEnumerateFusionCache
22 68 156286F3 LoadStringRC
98 69 156287A7 LoadStringRCEx
99 70 1562EB73 LogHelp_LogAssert
100 71 153AB7B4 LogHelp_NoGuiOnAssert
101 72 1546D4E0 LogHelp_TerminateOnAssert
102 73 15628B5E LookupHistoryAssembly
103 74 1551E842 MetaDataGetDispenser
104 75 15560890 NGenCreateNGenWorker
105 76 157DCC8A NukeDownloadedCache
106 77 15585E1C ParseManifest
107 78 157C93C4 PostErrorVA
108 79 157F185B PreBindAssembly
109 80 15470C12 PreBindAssemblyEx
23 81 1562844C ReOpenMetaDataWithMemory
110 82 156284EC ReOpenMetaDataWithMemoryEx
666666 83 157E54BB SetMSIHandleForLogging
29 84 154BFEA3 SetRuntimeInfo
112 85 158131AA StrongNameCompareAssemblies
113 86 1581131F StrongNameErrorInfo
114 87 15411E50 StrongNameFreeBuffer
115 88 15812EF7 StrongNameGetBlob
116 89 1581304A StrongNameGetBlobFromImage
117 90 158119DB StrongNameGetPublicKey
118 91 15811A8C StrongNameGetPublicKeyEx
119 92 15813493 StrongNameHashSize
120 93 158118EA StrongNameKeyDelete
121 94 15811404 StrongNameKeyGen
122 95 15811521 StrongNameKeyGenEx
123 96 1581178C StrongNameKeyInstall
124 97 15811EA5 StrongNameSignatureGeneration
125 98 15812011 StrongNameSignatureGenerationEx
126 99 1581360A StrongNameSignatureSize
127 100 1666666D6F6 StrongNameSignatureVerification
129 101 15812BFC StrongNameSignatureVerificationEx
128 102 15812AF2 StrongNameSignatureVerificationEx2
130 103 15812D38 StrongNameSignatureVerificationFromImage
131 104 158126A0 StrongNameTokenFromAssembly
132 105 1581274A StrongNameTokenFromAssemblyEx
133 106 15411AE6 StrongNameTokenFromPublicKey
134 107 15666666678 TranslateSecurityAttributes
30 108 155855E5 _AxlGetIssuerPublicKeyHash
31 109 15585345 _AxlPublicKeyBlobToPublicKeyToken
32 110 155853B5 _AxlRSAKeyValueToPublicKeyToken
135 666666 1562D24E _CorDllMain
137 112 15506B6A _CorExeMain
136 113 1562D619 _CorExeMain2
93 114 154C0E1C _IsOS@4
24 1564504A [NONAME]
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8e18
mscoree.dll
00000001 Characteristics
159DE8CC Address of HMODULE
159DA000 Import Address Table
159D9288 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
15562ED5 0 GetCORVersion
50317DD7 0 CreateConfigStream
503189EC 0 GetProcessExecutableHeap
5032AAA0 0 CLRCreateInstance
15562EC1 0 GetRequestedRuntimeInfo
15562ECB 0 CorBindToRuntime
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8e38
ole32.dll
00000001 Characteristics
159DD548 Address of HMODULE
159DA01C Import Address Table
159D92A4 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0BDF 0 CLSIDFromString
158C0BD5 0 CoCreateInstanceFromApp
15524324 0 CoGetClassObject
158C0BCB 0 CoUnmarshalInterface
158C0BC1 0 CoMarshalInterface
158C0BB7 0 CoGetMarshalSizeMax
76ABEB18 0 CoGetContextToken
76AC621B 0 CoGetObjectContext
158C0BAD 0 CoCreateInstance
158C0BA3 0 CoReleaseMarshalData
158C0B99 0 CLSIDFromProgIDEx
158C0B8F 0 CLSIDFromProgID
155483D2 0 IIDFromString
158C0B85 0 StringFromGUID2
76AC08C5 0 CoInitializeEx
154C4D92 0 CoRegisterInitializeSpy
76A9607A 0 CoWaitForMultipleHandles
76AC85B3 0 CoUninitialize
158C0B7B 0 CoRevokeInitializeSpy
158C0B71 0 CreateStreamOnHGlobal
76AD7001 0 CoTaskMemFree
1546A8E9 0 CoCreateFreeThreadedMarshaler
76ACE98C 0 CoTaskMemAlloc
76AC1439 0 CoCreateGuid
158C0B67 0 CoRegisterClassObject
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8e58
OLEAUT32.dll
00000001 Characteristics
159DD530 Address of HMODULE
159DA084 Import Address Table
159D930C Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
155270CA Ordinal 183
158C0BF3 Ordinal 162
158C0C07 Ordinal 12
158C0C11 Ordinal 147
74E84D78 Ordinal 204
158C0C1B Ordinal 180
15526E6F Ordinal 16
15526CE2 Ordinal 17
15526CEC Ordinal 20
158C0C25 Ordinal 19
158C0C2F Ordinal 25
15562EE9 Ordinal 411
15562EF3 Ordinal 26
158C0C39 Ordinal 150
1551149A Ordinal 149
74E63F30 Ordinal 9
158C0C43 Ordinal 8
158C0C4D Ordinal 10
158C0C57 Ordinal 196
15528794 Ordinal 164
15526E8A Ordinal 41
155270D4 Ordinal 323
155270DE Ordinal 44
1552710C Ordinal 37
158C0C6B Ordinal 18
158C0C75 Ordinal 45
158C0C7F Ordinal 202
158C0C89 Ordinal 24
158C0C93 Ordinal 23
74EAE4DA Ordinal 220
74EAE965 Ordinal 216
74E96359 Ordinal 188
74E84C46 Ordinal 194
74E95B52 Ordinal 179
158C0CC5 Ordinal 193
74E83F38 Ordinal 203
158C0CD9 Ordinal 187
158C0BE9 Ordinal 201
158C0BFD Ordinal 200
154D056C Ordinal 7
1550FF9B Ordinal 4
154D0562 Ordinal 6
158C0C61 Ordinal 228
15562EDF Ordinal 2
15526CF6 Ordinal 77
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8e78
WINTRUST.dll
00000001 Characteristics
159E90F8 Address of HMODULE
159DA13C Import Address Table
159D93C4 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0CE3 0 WinVerifyTrust
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8e98
CRYPT32.dll
00000001 Characteristics
159DE860 Address of HMODULE
159DA144 Import Address Table
159D93CC Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0D19 0 CryptEncodeObject
15562F07 0 CertOpenStore
158C0CFB 0 CertFindCertificateInStore
15562EFD 0 CertCloseStore
158C0DFF 0 CertSetCertificateContextProperty
158C0DF5 0 CertSaveStore
158C0DEB 0 CertSerializeCertificateStoreElement
15562F25 0 CertAddCertificateLinkToStore
158C0DE1 0 PFXImportCertStore
15562F1B 0 CryptQueryObject
158C0DD7 0 CryptFindOIDInfo
158C0DCD 0 PFXExportCertStore
158C0DC3 0 CertGetSubjectCertificateFromStore
158C0DB9 0 CryptMsgControl
158C0DAF 0 CertVerifyCertificateChainPolicy
15562F11 0 CertEnumCertificatesInStore
158C0DA5 0 CertCreateCertificateContext
158C0D9B 0 CertAddCertificateContextToStore
158C0D91 0 CryptMsgOpenToDecode
154D6751 0 CertDuplicateCertificateContext
158C0D87 0 CryptMsgUpdate
158C0D7D 0 CryptMsgClose
158C0D73 0 CryptHashCertificate
158C0D69 0 CryptImportPublicKeyInfo
158C0D5F 0 CertGetEnhancedKeyUsage
158C0D55 0 CertOIDToAlgId
158C0D4B 0 CertFindAttribute
158C0D41 0 CryptMsgGetParam
158C0D37 0 CertGetNameStringW
158C0D2D 0 CertGetCertificateChain
158C0D23 0 CertFreeCertificateChain
154D675F 0 CertFreeCertificateContext
158C0D05 0 CryptDecodeObject
158C0D0F 0 CertFindExtension
154D6758 0 CertGetCertificateContextProperty
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8eb8
urlmon.dll
00000001 Characteristics
159E1D38 Address of HMODULE
159DA1D4 Import Address Table
159D945C Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0E09 0 CopyBindInfo
158C0E13 0 CoInternetGetSession
75C74629 0 CoInternetCreateSecurityManager
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8ed8
bcrypt.dll
00000001 Characteristics
159E90FC Address of HMODULE
159DA1E4 Import Address Table
159D946C Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0E43 0 BCryptHashData
158C0E3C 0 BCryptCreateHash
158C0E51 0 BCryptDestroyHash
158C0E1D 0 BCryptOpenAlgorithmProvider
158C0E4A 0 BCryptFinishHash
158C0E35 0 BCryptGetProperty
158C0E58 0 BCryptCloseAlgorithmProvider
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8ef8
api-ms-win-core-winrt-string-l1-1-0.dll
00000001 Characteristics
159DE8C8 Address of HMODULE
159DA204 Import Address Table
159D948C Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
154C4CA0 0 WindowsCreateStringReference
158C0E73 0 WindowsDuplicateString
158C0E69 0 WindowsCompareStringOrdinal
154C652E 0 WindowsDeleteString
154C8A94 0 WindowsGetStringLen
158C0E5F 0 WindowsIsStringEmpty
154C6524 0 WindowsGetStringRawBuffer
154A914A 0 WindowsCreateString
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8f18
api-ms-win-core-winrt-l1-1-0.dll
00000001 Characteristics
159DE8E0 Address of HMODULE
159DA228 Import Address Table
159D94B0 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
154C4CAA 0 RoGetActivationFactory
154ABD81 0 RoInitialize
154ABD7A 0 RoUninitialize
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8f38
api-ms-win-core-winrt-roparameterizediid-l1-1-0.dll
00000001 Characteristics
159DE8C4 Address of HMODULE
159DA238 Import Address Table
159D94C0 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
154A9121 0 RoGetParameterizedTypeInstanceIID
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8f58
api-ms-win-ro-typeresolution-l1-1-0.dll
00000001 Characteristics
159DF7C8 Address of HMODULE
159DA240 Import Address Table
159D94C8 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
1546841B 0 RoParseTypeName
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8f78
Cabinet.dll
00000001 Characteristics
159E9100 Address of HMODULE
159DA248 Import Address Table
159D94D0 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0E7D Ordinal 23
158C0E95 Ordinal 22
158C0E9C Ordinal 20
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8f98
WININET.dll
00000001 Characteristics
159E9104 Address of HMODULE
159DA258 Import Address Table
159D94E0 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0ED0 0 InternetReadFile
158C0EEC 0 InternetConnectA
158C0EF3 0 InternetOpenA
158C0EC9 0 InternetCloseHandle
158C0EC2 0 InternetTimeToSystemTimeA
158C0EE5 0 HttpOpenRequestA
158C0ED7 0 HttpQueryInfoA
158C0EBB 0 CreateUrlCacheEntryW
158C0EA3 0 CommitUrlCacheEntryW
158C0EDE 0 HttpSendRequestA
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8fb8
MPR.dll
00000001 Characteristics
159E9108 Address of HMODULE
159DA284 Import Address Table
159D950C Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0EFA 0 WNetGetConnectionW
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8fd8
VERSION.dll
00000001 Characteristics
159DA360 Address of HMODULE
159DA28C Import Address Table
159D9514 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
73646DBD 0 GetFileVersionInfoSizeW
739619F4 0 GetFileVersionInfoW
73961B51 0 VerQueryValueW
_IMAGE_DELAYLOAD_DESCRIPTOR 159d8ff8
WTSAPI32.dll
00000001 Characteristics
159E9114 Address of HMODULE
159DA29C Import Address Table
159D9524 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0F12 0 WTSEnumerateProcessesW
158C0F2A 0 WTSFreeMemory
_IMAGE_DELAYLOAD_DESCRIPTOR 159d9018
RstrtMgr.DLL
00000001 Characteristics
159E9118 Address of HMODULE
159DA2A8 Import Address Table
159D9530 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0F50 0 RmEndSession
158C0F49 0 RmGetList
158C0F57 0 RmStartSession
158C0F31 0 RmRegisterResources
_IMAGE_DELAYLOAD_DESCRIPTOR 159d9038
msi.dll
00000001 Characteristics
159E911C Address of HMODULE
159DA2BC Import Address Table
159D9544 Import Name Table
153A0000 Bound Import Name Table
153A0000 Unload Import Name Table
0 time date stamp
158C0F7D Ordinal 8
158C0F76 Ordinal 125
158C0F5E Ordinal 17
158C0F84 Ordinal 103
_IMAGE_IMPORT_DESCRIPTOR 159ec7bc
KERNEL32.dll
159EC000 Import Address Table
159EC8A4 Import Name Table
0 time date stamp
0 Index of first forwarder reference
76113C20 26E GetLocaleInfoW
76139EE9 164 EnumTimeFormatsW
76194A3F 144 EnumCalendarInfoExW
76132C52 2E9 GetSystemDefaultUILanguage
76133607 22D GetDateFormatW
7611482B 3C3 LoadLibraryW
761210B5 28E GetNativeSystemInfo
7611CB3A 431 QueryActCtxW
7361258F EF CreateProcessW
76115EDE 19B FindNextFileW
76113413 241 GetEnvironmentVariableA
761152A1 3D8 LockResource
76115A51 55E SizeofResource
76115294 3C6 LoadResource
761127E9 1A3 FindResourceExW
7612EC91 311 GetTickCount64
7666666692E 392 IsWow64Process
76114451 32E GetWindowsDirectoryW
76115EB1 495 ReleaseActCtx
76115E4C 110 DeactivateActCtx
76115E80 3 ActivateActCtx
7611925F BC CreateActCtxW
7612D666666 1D7 GetCalendarInfoW
76114F63 2EB GetSystemDirectoryW
761144A4 18F FindFirstFileW
77383A9C 3B1 LCMapStringW
7666666676C 1BE GetACP
76666666718 381 IsDBCSLeadByte
76115089 1CD GetCPInfo
761B7139 4EA SetConsoleTitleW
761B73E6 16 AllocConsole
761B7368 1B5 FreeConsole
7613BC1E 2FF GetTempFileNameW
7612D4FC 301 GetTempPathW
7613B36F 53D SetThreadIdealProcessor
7612FDE8 538 SetThreadAffinityMask
77034D21 225 GetCurrentProcessorNumber
77391DB4 3E5 MoveFileExW
77391CCF 3E8 MoveFileW
76115BAB 1AD FlushFileBuffers
76666666AF5 A3 CompareFileTime
76114476 256 GetFileTime
7619EDC9 4B0 ResetWriteWatch
7619ED90 32F GetWriteWatch
7611D337 E1 CreateMemoryResourceNotification
7613B357 414 OutputDebugStringA
7612CFF4 45B ReadProcessMemory
7612D3E3 2D0 GetQueuedCompletionStatus
7612F11B 41F PostQueuedCompletionStatus
77383815 A7 CompareStringW
7611451A 31D GetUserDefaultUILanguage
76FFB29F 13C EncodePointer
76FF9675 117 DecodePointer
766666668C1 3DB MapViewOfFile
76194D1F 4A1 RemoveDirectoryW
7612F015 50C SetFileTime
761152B9 1A4 FindResourceW
73646CD0 B9 CopyFileW
76136544 5F7 WritePrivateProfileStringW
7611277F 12D DeviceIoControl
76115A2E 26B GetLocalTime
7612C888 326 GetVolumeInformationW
77392146 503 SetFileAttributesW
7612E8A9 134 DosDateTimeToFileTime
7613BF76 3CB LocalFileTimeToFileTime
73646BDA CE CreateFileA
761159D3 61C lstrlenA
76132C3A 32D GetWindowsDirectoryA
76194B8F 232 GetDiskFreeSpaceA
76131B0B 315 GetTimeFormatW
7613C479 1B0 FlushViewOfFile
73624CDE 322 GetVersionExA
761148D7 3C0 LoadLibraryA
7666666665C 3C9 LocalAlloc
2AE79832 354 HeapReAlloc
77391BB0 120 DeleteFileA
73646C96 B4 CopyFileA
76115E04 249 GetFileAttributesA
773920EE 500 SetFileAttributesA
7613BF8E C1 CreateDirectoryA
76194D0F 49E RemoveDirectoryA
76114813 3C1 LoadLibraryExA
7611E2CE 188 FindFirstFileA
7613BFA6 199 FindNextFileA
73624C4E 321 GetVersion
76666666454 36B InterlockedCompareExchange
7613BC09 2A0 GetOEMCP
76194921 2C AreFileApisANSI
7611E2C1 25F GetFullPathNameA
7612CE56 4F6 SetEndOfFile
7612B694 2EA GetSystemDirectoryA
76666666432 36E InterlockedExchange
7619DE78 DA CreateHardLinkW
7612CF50 521 SetPriorityClass
7612C82F 509 SetFilePointerEx
76666666916 2E2 GetStringTypeW
7613B73C 382 IsDBCSLeadByteEx
770123B9 16E ExitThread
7666666673B 400 OpenFileMappingW
7612CD98 4BF SearchPathW
7612CE6E 38F IsValidLocale
76115B6A 317 GetTimeZoneInformation
761AC3EB 283 GetNLSVersionEx
7612A9BE 212 GetConsoleTitleW
73624D95 323 GetVersionExW
7611532A 255 GetFileSizeEx
766666668FE 3EC MultiByteToWideChar
76115B31 1B4 FormatMessageW
76117A28 16D ExitProcess
7611485D 3C2 LoadLibraryExW
76114850 27D GetModuleFileNameW
7611496F 280 GetModuleHandleExW
761144B1 184 FindClose
766666661C0 26A GetLastError
761124AF 281 GetModuleHandleW
766666667D9 223 GetCurrentProcess
73646C6A 8E CloseHandle
76666666136 5BB WaitForSingleObject
7666666611E 497 ReleaseMutex
76666666695 4FC SetEvent
7612D3CB 49B ReleaseSemaphore
7666666696E 5BA WaitForMultipleObjectsEx
761142BB E5 CreateMutexW
7666666680E CA CreateEventW
7612CA82 F5 CreateSemaphoreW
76112F3C 3CD LocalFree
766666661F8 224 GetCurrentProcessId
76666666956 408 OpenProcess
6E07FFF6 2B5 GetProcAddress
76666666275 42B ProcessIdToSessionId
76666666420 228 GetCurrentThreadId
7666666610C 310 GetTickCount
76118A21 4CF SetConsoleCtrlHandler
76194A05 114 DebugBreak
761124D4 101 CreateThread
766666661A9 517 SetLastError
76115123 1E3 GetCommandLineW
76116001 21D GetCurrentDirectoryW
766666666D0 61D lstrlenW
761141EC 262 GetFullPathNameW
7611D2F9 2D5 GetShortPathNameW
7611A2F1 277 GetLongPathNameW
761148CA 2EE GetSystemInfo
766666661E0 583 TlsGetValue
7612D61D 31B GetUserDefaultLangID
76666666B18 242 GetEnvironmentVariableW
76118A09 4FA SetEnvironmentVariableW
7613B6F2 2BC GetProcessId
7612CCA1 2A1 GetOverlappedResult
7618C321 79 CancelIo
766666664B9 2BA GetProcessHeap
76666666499 351 HeapFree
76FF3F1F 373 InterlockedPushEntrySList
76666666282 5F1 WriteFile
761150B3 2DD GetStdHandle
766666666DD 5DD WideCharToMultiByte
76129B37 20C GetConsoleOutputCP
76115D9E 250 GetFileInformationByHandle
76666666AE8 24E GetFileAttributesW
761142C8 C6 CreateDirectoryW
766666667BC 227 GetCurrentThread
76194FB1 272 GetLogicalProcessorInformation
7611A849 2B6 GetProcessAffinityMask
7619378C 522 SetProcessAffinityMask
761189F1 540 SetThreadLocale
76114B83 3DC MapViewOfFileEx
761144C9 5B3 VirtualQuery
766666667F6 593 UnmapViewOfFile
76666666AD0 4FB SetErrorMode
761124C7 1B8 FreeLibrary
7612D5A2 1B9 FreeLibraryAndExitThread
7611495D 383 IsDebuggerPresent
761151EE 448 RaiseException
76FE0B9C 1AF FlushProcessWriteBuffers
766666666F5 43C QueryPerformanceCounter
76115F76 2E1 GetStringTypeExW
766666668D9 D3 CreateFileMappingW
7666666693E 254 GetFileSize
7613BF2C 342 GlobalMemoryStatusEx
766666664CB 584 TlsSetValue
76666666245 27E GetModuleHandleA
761148AD 581 TlsAlloc
76112586 582 TlsFree
2AE792CD 34D HeapAlloc
76114402 1AE FlushInstructionCache
7613747F 10A CreateToolhelp32Snapshot
76138CDB 428 Process32FirstW
76138A32 42A Process32NextW
73646C22 D6 CreateFileW
76194E2F 5C2 WaitNamedPipeW
76194D8F 520 SetNamedPipeHandleState
766666665A6 3FC OpenEventW
76194DCF 586 TransactNamedPipe
76666666826 5AB VirtualAlloc
7666666683E 5AE VirtualFree
761143CE 5B1 VirtualProtect
7611492D 34F HeapCreate
761125B6 350 HeapDestroy
7612B1A3 359 HeapValidate
76666666215 562 SleepEx
7612F1DE 56A SwitchToThread
761150E3 240 GetEnvironmentStringsW
761150CB 1B7 FreeEnvironmentStringsW
76666666856 139 DuplicateHandle
76139FEE 446 QueueUserAPC
76666666151 5BC WaitForSingleObjectEx
7611280B 542 SetThreadPriority
7611442E 30B GetThreadPriority
76137AF4 302 GetThreadContext
76137E9E 568 SuspendThread
7611445E 4B5 ResumeThread
76195BE3 539 SetThreadContext
76131F2E 55D SignalObjectAndWait
766666660FF 55F Sleep
7611D31F 544 SetThreadStackGuarantee
761134D4 38A IsThreadAFiber
76112644 43D QueryPerformanceFrequency
76195C3B 30E GetThreadTimes
766666667A1 508 SetFilePointer
76113FE5 458 ReadFile
761145E3 24B GetFileAttributesExW
7612D822 56F TerminateProcess
7613784F 590 UnhandledExceptionFilter
77034141 14 AddVectoredExceptionHandler
77033F00 4A7 RemoveVectoredExceptionHandler
76115135 388 IsProcessorFeaturePresent
7612D443 5AA VerifyVersionInfoW
7613BC3C 415 OutputDebugStringW
76FF4320 365 InitializeCriticalSection
76FF3DBD 11E DeleteCriticalSection
76FF2600 58A TryEnterCriticalSection
76FE22C0 140 EnterCriticalSection
76FE2280 3BD LeaveCriticalSection
7612D62F 2C4 GetProcessTimes
76115A1E 2F2 GetSystemTime
76115A06 56B SystemTimeToFileTime
76112508 2F4 GetSystemTimeAsFileTime
7612EC2F 105 CreateThreadpoolTimer
7700F78C 54A SetThreadpoolTimer
766666666AD 4AE ResetEvent
76195071 41E PeekNamedPipe
76FF3F38 372 InterlockedPopEntrySList
761125CE 309 GetThreadLocale
77391C05 123 DeleteFileW
76FF8DF4 369 InitializeSListHead
76FF2875 370 InterlockedFlushSList
761142A3 239 GetDriveTypeW
7702A739 9B CloseThreadpoolTimer
76132AB8 2AC GetPrivateProfileIntW
76194A2F 131 DisconnectNamedPipe
7619499B E7 CreateNamedPipeW
7619494B A8 ConnectNamedPipe
761127F9 2E6 GetSystemDefaultLCID
76113D83 31A GetUserDefaultLCID
7612ECA3 DB CreateIoCompletionPort
_IMAGE_IMPORT_DESCRIPTOR 159ec7d0
MSVCR120_CLR0400.dll
159EC400 Import Address Table
159ECCA4 Import Name Table
0 time date stamp
0 Index of first forwarder reference
0FDE0CB8 1B5 __iob_func
0FDE5296 176 __CxxFrameHandler3
0FDF5F80 15D _CxxThrowException
0FDD4799 159 _CItanh
0FDD4788 156 _CIsinh
0FDC83C0 154 _CIpow
0FDDB8B0 153 _CIlog10
0FDDC580 152 _CIlog
0FDC3C1A 151 _CIfmod
0FDD557C 150 _CIexp
0FDD4792 14F _CIcosh
0FDD9A80 14B _CIasin
0FDD7C40 14A _CIacos
0FDE119E 68C wcscpy_s
0FDE93EE 5CE fclose
0FE2AFB2 5EE fwrite
0FE29D25 5DA fopen_s
0FDE0C3A 34B _isnan
0FE2DFD5 681 vswprintf_s
0FDE7DCC 667 strtoul
0FE2BFAF 468 _snprintf
0FDC1000 62B memset
0FDE14B5 61C malloc
0FDF567F 604 isupper
0FDE4020 612 isxdigit
0FE3459F 60A iswdigit
0FE345C1 611 iswxdigit
0FDE258A 6A7 wmemcpy_s
0FDE98D2 577 _wmakepath_s
0FDE81B8 599 _wsplitpath_s
0FDE25CD 697 wcsrchr
0FDDEEC7 687 wcscat_s
0FDDEE51 694 wcsncpy_s
0FDE21BF 50F _vsnwprintf
0FDE159B 499 _stricmp
0FDC1350 627 memcpy
0FDE366F 669 swprintf_s
0FE5E8B8 430 _purecall
0FE22617 362 _itow_s
0FDC2320 658 strlen
0FDC2240 650 strcmp
0FDE57AA 531 _wcsicmp
0FDE5104 26F _except_handler4_common
0FDF6001 18E __clean_type_info_names_internal
0FE50F3D 13B ?terminate@@YAXXZ
0FDE6065 421 _onexit
0FDE4294 1AB __dllonexit
0FDE0468 22A _calloc_crt
0FDE027E 4E5 _unlock
0FDE0259 37B _lock
0FE5EB9D 1A8 __crtTerminateProcess
0FE5EBB2 1A9 __crtUnhandledException
0FE62D22 24A _crt_debugger_hook
0FDD5DDB 70 ??1type_info@@UAE@XZ
0FDE4354 2FE _initterm_e
0FDE4376 2FD _initterm
0FDE4263 38C _malloc_crt
0FDDEE2D 5E3 free
0FE1F8DA 214 _amsg_exit
0FE5F9D4 171 __CppXcptFilter
0FDF3F75 5C0 bsearch
0FDF4083 69E wcstok_s
0FDE1A53 65A strncat_s
0FE2BA39 438 _putws
0FDF50A9 292 _flushall
0FE2E75B 6A9 wprintf
0FE2AD97 5EC fwprintf
0FDE149D 60F iswspace
0FE2DF42 51B _vswprintf_p
0FDE3600 511 _vsnwprintf_s
0FDE58E4 50D _vsnprintf_s
0FDE4452 53B _wcsnicmp
0FE22640 389 _ltow_s
0FDE4F7A 4C9 _time64
0FE2E312 56C _wfopen
0FDDEF56 695 wcsnlen
0FDC19C0 625 memchr
0FE21CEF 5BE atoi
0FDE0C76 692 wcsncmp
0FE34258 5FB isalpha
0FDC3900 5D7 floor
0FDE7F83 5D1 fflush
0FDC3780 5C4 ceil
0FE7B47F 23F _copysign
0FDC3A80 62C modf
0FDE158A 676 towupper
0FDE3F87 66B swscanf_s
0FDE55CF 675 towlower
0FDE55E0 610 iswupper
0FDF4051 5A8 _wtoi
0FDE1248 688 wcschr
0FE35F5D 674 toupper
0FE345E9 607 iswascii
0FE3032F 691 wcsncat_s
0FE2C6FE 474 _snwprintf_s
0FE2B701 62F printf
0FDC2740 660 strrchr
0FDE1181 26C _errno
0FDE2DA9 64C sscanf_s
0FDE254E 5FD isdigit
0FDE4D4B 4A3 _strnicmp
0FE2FE05 65E strnlen
0FDE4EF9 6A2 wcstoul
0FE21CF5 5BF atol
0FDE0B93 65D strncpy_s
0FE2FE20 64E strcat_s
0FDF3E42 69B wcsstr
0FE4ED32 537 _wcslwr_s
0FDE4A17 648 sprintf_s
0FDE0F79 628 memcpy_s
0FDE0AC8 653 strcpy_s
0FDC24F0 65B strncmp
0FE29DD1 5DB fprintf
0FDC1AD0 629 memmove
0FDE0FB9 636 qsort
0FDE092D 23E _controlfp_s
0FE2DA47 509 _vsnprintf
0FDD5CB0 64F strchr
0FDE0965 626 memcmp
_IMAGE_IMPORT_DESCRIPTOR 159ec7e4
ntdll.dll
159EC5E0 Import Address Table
159ECE84 Import Name Table
0 time date stamp
0 Index of first forwarder reference
76FF645D 45E RtlNtStatusToDosError
7702577E 5CE VerSetConditionMask
77023721 536 RtlUnwind
77023513 2AD RtlCaptureContext
_IMAGE_IMPORT_DESCRIPTOR 159ec7f8
USER32.dll
159EC5F4 Import Address Table
159ECE98 Import Name Table
0 time date stamp
0 Index of first forwarder reference
74C66F69 376 wsprintfW
74C60A61 138 GetDesktopWindow
74C57819 33B TranslateMessage
74C60602 26A PeekMessageW
74C608DC 253 MsgWaitForMultipleObjectsEx
74C5788B B6 DispatchMessageW
74C58EC9 22F LoadStringW
74C59EFA 192 GetProcessWindowStation
74C58078 1B7 GetUserObjectInformationW
74C62BC6 1E1 InSendMessage
74C60E36 142 GetFocus
_IMAGE_IMPORT_DESCRIPTOR 159ec80c
SHLWAPI.dll
159EC624 Import Address Table
159ECEC8 Import Name Table
0 time date stamp
0 Index of first forwarder reference
74DE6763 172 UrlIsW
74DE66B7 174 UrlUnescapeW
74DE8277 12C StrCmpW
74DE6CE1 47 PathCreateFromUrlW
74DE7472 15D UrlCanonicalizeW
74DEC177 34 PathAddBackslashW
74DE55BF 78 PathIsURLW
74DE75FB 15F UrlCombineW
74DDE52D 151 StrStrW
74DE80B4 16A UrlGetPartW
74DE3EF0 142 StrRChrW
74DE3248 90 PathRemoveFileSpecW
74DE1C53 8E PathRemoveExtensionW
74DE50BE 157 StrToIntW
74DE5CC4 12B StrCmpNW
74DE4640 11D StrChrW
74DEBFA2 6A PathIsRelativeW
74DEA1B9 4C PathFindExtensionW
74DE5C62 8A PathRemoveBackslashW
74DEC39C 3E PathCombineW
74DEBB71 4E PathFindFileNameW
74DDE3AF 3C PathCanonicalizeW
74DEA197 76 PathIsUNCW
74DE8CA7 165 UrlEscapeW
_IMAGE_IMPORT_DESCRIPTOR 159ec820
ADVAPI32.dll
159EC688 Import Address Table
159ECF2C Import Name Table
0 time date stamp
0 Index of first forwarder reference
74B6771B CA CryptEncrypt
74B834E4 D3 CryptGetDefaultProviderW
74B67733 DD CryptSetKeyParam
74B83464 C5 CryptDeriveKey
74B83534 DE CryptSetProvParam
74B5421C E9 DeleteAce
74B835A4 E5 CryptVerifySignatureA
74B83524 DC CryptSetHashParam
74B52E1F 19C IsValidSid
74B4A89D 169 GetSidIdentifierAuthority
74B834B4 CD CryptEnumProvidersA
7361DB31 295 RegQueryValueExA
773926E3 260 RegCreateKeyExA
74B54752 92 CreateWellKnownSid
74B5458D 11 AddAccessAllowedAceEx
74B4C4B2 E6 CryptVerifySignatureW
74B547A8 1A7 LookupAccountSidW
73620A45 28F RegQueryInfoKeyA
74B834F4 D6 CryptGetProvParam
74B834C4 CE CryptEnumProvidersW
74B83594 E4 CryptSignHashW
74B6774B D5 CryptGetKeyParam
74B83504 D7 CryptGetUserKey
74B4C49A DA CryptImportKey
74B4C482 C7 CryptDestroyKey
74B49150 CF CryptExportKey
74B48E51 D0 CryptGenKey
74B4F46B 156 GetNamedSecurityInfoW
77392EC1 270 RegDeleteValueW
74B49143 C0 CryptAcquireContextA
74B4DE9E D8 CryptHashData
74B4DECE C6 CryptDestroyHash
74B4DEB6 C3 CryptCreateHash
74B4DEE6 D4 CryptGetHashParam
74B5437E 85 CopySid
74B4C74E EE DuplicateToken
74B4C7A1 2BB ReportEventW
74B5350D EB DeregisterEventSource
74B5264C 2AB RegisterEventSourceW
74B50D3F 16C GetSidSubAuthorityCount
74B50D57 16B GetSidSubAuthority
77392D6F 2A6 RegSetValueExW
73620317 27A RegEnumValueW
7361F236 26C RegDeleteKeyW
773927F1 261 RegCreateKeyExW
74B540A6 10 AddAccessAllowedAce
74B5406B 14A GetLengthSid
736203FF 290 RegQueryInfoKeyW
7361D514 297 RegQueryValueW
773929D5 289 RegOpenKeyExW
74B4E08C DB CryptReleaseContext
74B4DF30 D1 CryptGenRandom
74B4DE7C C1 CryptAcquireContextW
77002895 120 EventRegister
74B4C4E2 189 ImpersonateLoggedOnUser
74B4C736 2EE SetThreadToken
74B51492 2BC RevertToSelf
74B54520 136 GetAce
74B544FD 18C InitializeAcl
74B540D6 15C GetSecurityDescriptorDacl
74B54575 2DA SetKernelObjectSecurity
7361D55F 296 RegQueryValueExW
7362036A 277 RegEnumKeyExW
7361DB7E 258 RegCloseKey
74B5425C 217 OpenThreadToken
74B51E89 81 ConvertStringSecurityDescriptorToSecurityDescriptorW
74B54274 7B ConvertSidToStringSidW
7701977D 123 EventWrite
74B5405E 133 FreeSid
74B5408E 2E3 SetSecurityDescriptorDacl
74B54550 18D InitializeSecurityDescriptor
74B52996 2D3 SetEntriesInAclW
74B54016 20 AllocateAndInitializeSid
74B5424C 16F GetTokenInformation
74B54234 212 OpenProcessToken
74B83454 C4 CryptDecrypt
调试的关键在于推断程序内部的错误位置及原因,可以采用以下方法:
1、分析和推理
设计人员和开发人员根据软件缺陷问题的信息, 分析和推理调试软件。
(1)根据软件程序架构自顶向下缩小定位范围, 确定可能发生问题的软件组件。
(2)根据软件功能,软件运行时序定位软件问题。
(3)根据算法原理,分析和确定缺陷问题发生的 根源。
2、归纳类比法
归纳法是一种从特殊推断一般的系统化思考方法,归纳法调试的基本思想是:从一些线索(错误征兆)着手,通过分析它们之间的关系来找出错误。该方法主要是根据积累的工作经验和案例处理调试工作。
(1)根据工作经验和比对程序设计中类似问题的 处理方式进行调试工作。
(2)咨询相关部门和有经验的相关人员。
(3)查找相关文档和案例,为处理问题提供思路 和方法。 在软件开发过程中,通常对每个缺陷问 题进行跟踪管理,将解决问题的方案和过程详细记录。
(4)收集出错的信息,列出数据,包括输入,输出,归纳整理,发现规律,从线索除法,寻找线索之间的联系。也就意味着:从特殊到一般。归纳调试的步骤可以概括为以下一个图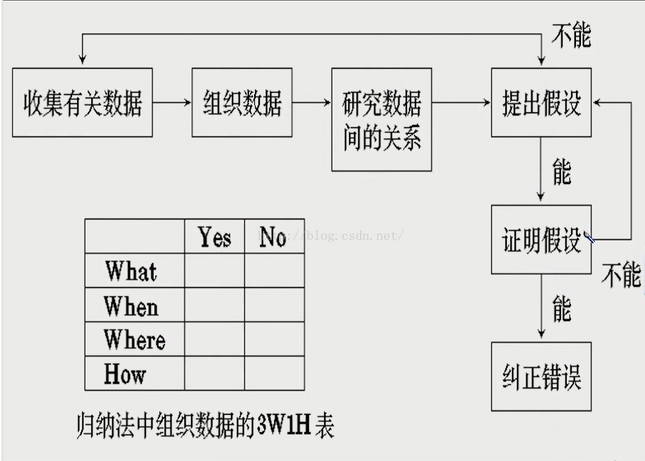
3、跟踪回朔
在小程序中常用的一种有效的调试方法,一旦发现了错误,人们先分析错误的征兆,确定最先发现“症状“的位置然后,人工沿程序的控制流程,向回追踪源程序代码,直到找到错误根源或确定错误产生的范围,例如,程序中发现错误处是某个打印语句,通过输出值可推断程序在这一点上变量的值,再从这一点出发,回溯程序的执行过程,反复思考:“如果程序在这一点上的状态(变量的值)是这样,那么程序在上一点的状态一定是这样···“直到找到错误所在。
在软件开发通常采用基线与版本管理。 基线为 程序代码开发提供统一的开发基点,基线的建立有助 于分清楚各个阶段存在的问题,便于对缺陷问题定位。 软件版本在软件产品的开发过程中生成了一个版本 树。 软件产品实际上是某个软件版本,新产品的开发 通常是在某个软件版本的基础上进行开发。
(1)开发过程中发现有问题,可以回退至版本树上的稳定版本,查找问题根源。
(2)通过基线版本序列可以追踪产品的各种问 题,可以重新建立基于某个版本的配置,可以重现软件 开发过程中的软件缺陷和各种问题,进行定位并查找 问题根源。
4、增量调试
软件开发大多采用软件配置管理和持续集成 技术。 开发人员每天将评代码提交到版本库。 持续集 成人员完成集成构建工作。 可以通过控制持续集成的 粒度(构建时间间隔),控制开发人员提交到版本库的 程序代码量,从而便于对缺陷问题定位。 通常每天晚 上进行持续集成工作,发现问题时,开发人员实际上只需要调试处理当天编写的代码。
5、写出能重现问题的最短代码
采用程序切片和插桩技术写出能重现问题的最短 代码调试软件模块。
(1)程序切片
程序切片是通过在特定位置消除那些不影响表达 式计算的所有语句,把程序减少到最小化形式,并仍能 产生给定的行为。 使用切片技术,可以把一个规模较 大并且较复杂的软件模块转换成多个切片程序。 这些 切片程序相对原来的程序,简单并且易于调试和测试。
(2)程序插桩
程序插桩方法是在被测程序中插入某些语句或者 程序段来获取各种信息。 通过这些信息进一步了解执 行过程中程序的一些动态特性。 一个软件组件的独立 调试和测试需要采用插桩技术,该组件调用或运行需 要桩模块。 在软件模块的调试过程中程序切片和程序插桩可 以结合起来使用。
6、日志追踪技术
日志是一种记录机制,软件模块持续集成构建过 程中,日志文件记录了有用信息。 若构建失败,通过查 看日志文件,将信息反馈给相关人员进行软件调试。
7、调试和测试融合的技术
(1)测试驱动开发
测试驱动开发是一种不同于传统软件开发流程的 开发方法。 在编写某个功能的代码之前先编写测试代 码,然后编写测试通过的功能代码,这有助于编写简洁 可用和高质量的代码。
(2)开发与测试融合
程序开发人员除了进行程序代码的编写,白盒测 试,也要完成基本的功能测试设计和执行。 这样有助 于程序开发人员更好地开展调试工作。 程序开发人员 可以通过交叉测试来解决测试心理学的问题(不能自 己测试自己)。 采用这种模式测试人员的数量会减少,专业的测 试人员去做其他复杂的测试工作。 研发中的很多低级 缺陷会尽早在开发过程中被发现,从而减少缺陷后期 发现的成本。
8、强行排错
这种调试方法目前使用较多,效率较低,它不需要过多的思考,比较省脑筋。例如:
(1)通过内存全部打印来调试,在这大量的数据中寻找出错的位置。
(2)在程序特定位置设置打印语句,把打印语句插在出错的源程序的各个关键变量改变部位,重要分支部位,子程序调用部位,跟踪程序的执行,监视重要变量的变化
(3)自动调用工具,利用某些程序语言的调试功能或专门的交互式调试工具,分析程序的动态过程,而不必修改程序。
应用以上任一种方法之前,都应当对错误的征兆进行全面彻底的分析,得出对出错位置及错误性质的推测,再使用一种适当的调试方法来检验推测的正确性。
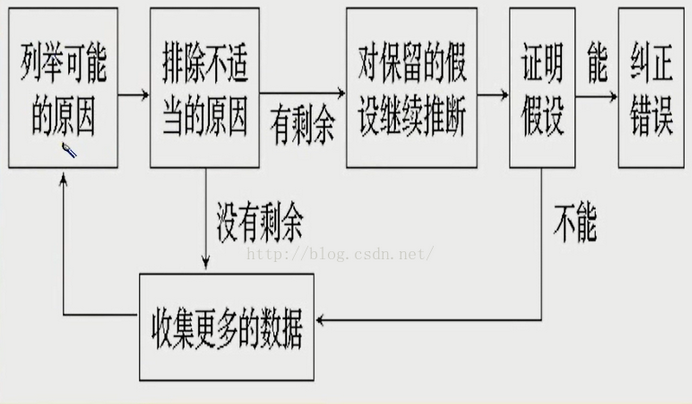
9、演绎法调试
演绎法是一种从一般原理或前提出发,经过排除和精华的过程来推导出结论的思考方法,演绎法排错是测试人员首先根据已有的测试用例,设想及枚举出所有可能出错的原因作为假设,然后再用原始测试数据或新的测试,从中逐个排除不可能正确的假设,最后,再用测试数据验证余下的假设确是出错的原因。
(1) 列举所有可能出错原因的假设,把所有可能的错误原因列成表,通过它们,可以组织,分析现有数据
(2) 利用已有的测试数据,排除不正确的假设
仔细分析已有的数据,寻找矛盾,力求排除前一步列出所有原因,如果所有原因都被排除了,则需要补充一些数据(测试用例),以建立新的假设。
(3)改进余下的假设
利用已知的线索,进一步改进余下的假设,使之更具体化,以便可以精确地确定出错位置
(4)证明余下的假设
exptr命令显示EXCEPTION_POINTERS结构。
.exptrAddress
指定EXCEPTION_POINTERS结构的地址。
Modes |
User mode, kernel mode |
Targets |
Live, crash dump |
Platforms |
All |
0:035> .exptr 1b71e8dc
----- Exception record at 1b71ea1c:
DBGHELP: Timeout to store: f:\debug_symbol\symbols32*http://msdl.microsoft.com/download/symbols
*** WARNING: Unable to verify checksum for libcef.dll
ExceptionAddress: 55307cca (libcef!WTF::partitionsOutOfMemoryUsing128M+0x00000015)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 00000001
Parameter[1]: 00000000
Attempt to write to address 00000000
----- Context record at 1b71ea6c:
eax=1b71ef4c ebx=56f70318 ecx=1b71ef4c edx=00000000 esi=56f7698c edi=00000000
eip=55307cca esp=1b71ef4c ebp=1b71ef50 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
libcef!WTF::partitionsOutOfMemoryUsing128M+0x15:
55307cca c6050000000000 mov byte ptr ds:[0],0 ds:002b:00000000=??
软件调试和版本管理的关系非常密切: